Security Camp Kyushu in Fukuoka 2015
“Security Camp Kyushu in Fukuoka 2015” was held at Kyushu University Nishijin Plaza from August 28th to 30th.
Click here for [Security Camp Implementation Council HP] Click here for 【Event Report (Kyushu University Cyber Security Center)】
1. Outline of the event


Figure 1 Scenery of the general lecture venue (left) Figure 2 Greetings from the director (right)
| day & Time | General course | Friday, August 28, 2015 9:30~15:10 |
| Training camp course | Friday, August 28, 2015 13:30~18:30 | |
| Saturday, August 29, 2015 9:00~19:30 | ||
| Sunday, August 30, 2015 9:00~17:00 | ||
| Venue | Kyushu University Nishijin Plaza | |
| participant | General course | 87 people |
| Training camp course | 19 people | |
| Organizer | Security Camp Kyushu Implementation Council | |
| Security Camp Committee | ||
| Cybersecurity Center of Kyushu University(CSC) | ||
| Information-technology Promotion Agency(IPA) | ||
| Sponsorship | Kyushu Economic Federation | |
| Kyushu Bureau of Economy, Trade and Industry | ||
| Fukuoka Prefecture | ||
General course program
| 9:30 | opening | |
| Security Camp Committee Greetings from Secretary General | ||
| Organizer representative Greetings from Director Okamura
(Cyber Security Center) |
||
| Supporting representative Greetings from Mr. Tanaka
(Kyushu Bureau of Economy, Trade and Industry) |
||
| 10:00 | Keynote speech① | |
| “Information security threats approaching individuals-what do you think about it?” | IPA Technology Headquarters Security Center Investigator Shinichiro Kagaya |
|
| 11:00 | Keynote speech② | |
| “Basic Cyber Security Law and Message to Companies” | 経済産業省商務情報政策局情報セキュリティ政策室 課長補佐 山下浩司 |
|
| 11:30 | Keynote speech③ | |
| “In-house information management and legal responsibility” | 弁護士法人向原・川上総合法律事務所 弁護士 吉井和明 |
|
| 13:45 | Keynote speech④ | |
| “Information security measures-issues hidden in the home” | 株式会社シーアイエー 社長 平原隆 |
|
| 14:40 | Lightning talk(Security camp graduate) | |
| 15:10 | Closing | |
Training camp course program
| ▶ First day | |
| “Security Basics” ”Pcap data analysis” | Cyber University
Professor. Michio Sonoda |
| ▶ the 2nd day | |
| “Basics of Web Programming” ”Web Security Basics & Practice” | CIA Co., Ltd. Yuichi Hattori |
| “Let’s think about how to use information security technology in a case” | Attorney at law corporation Mukaihara / Kawakami Law Office
lawyer. Kazuaki Yoshii |
| ▶ Third day | |
| “Let’s play with it, break it, and become a hacker (Part 1)” “Let’s play with it, break it, and become a hacker (Part 2)” |
Kyushu Institute of Technology Graduate School
Associate professor. Hiroshi Koide |
2.Outline of the event
General course
“Information security threats approaching individuals-what do you think about them?”
In this lecture, explanations were given with demonstrations of damage cases related to smartphones, which have been rapidly spreading in recent years, and countermeasures on the user side.
“Basic Cyber Security Law and Message to Companies”
In this lecture, the measures taken by the Ministry of Economy, Trade and Industry to support cyber security measures in companies and the efforts to formulate cyber security management guidelines under consideration were explained.
“In-house information management and legal responsibility”
In this lecture, legal responsibilities, legal measures, preventive measures, etc. when managing information within a company were explained.
“Information security measures-issues hidden in the home”
In this lecture, explanations were given on security attacks and countermeasures in companies, including the experience of the Cyber Security Countermeasures Office of the National Police Agency and cases that occurred between parents and children of the lecturer.
Training camp course
“Security basics” “pcap data analysis”
In this course, after explaining basic network security, exercises were conducted to learn past attack patterns through analysis of packet analysis tools (Wireshark) and packets (pacp data).
“Web Programming Basics” “Web Security Basics & Practice”
In this course, after learning about the basic web mechanism and web programming through the development of a web application with a simple chat function, exercises will be conducted to learn countermeasures for vulnerabilities through attacks on vulnerable websites.
“Let’s think about how to use information security technology in a case”
In this course, a mock trial-style exercise was conducted to learn legal responsibility, legal coping, and preventive measures through past cases of information leakage.
“Let’s play with it, break it, and become a hacker (Part 1)”
“Let’s play with it, break it, and become a hacker (Part 2)”
In this course, you will learn about computers and electronic circuits by touching on both hardware and software technologies such as wiring resistors and programming to turn on / off LEDs using a small actual server (Raspberry Pi2) or breadboard. Basic exercises were conducted to become a hacker who has specialized knowledge and can clear technical issues.
General comment


General course
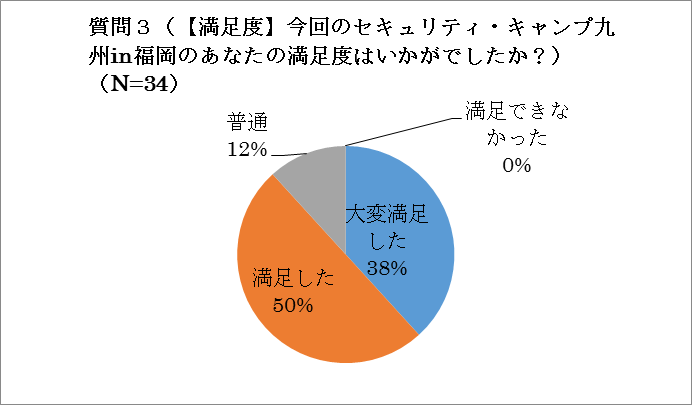
In the midst of large-scale information leakage incidents these days, I felt that the general lectures were enriched to help students and corporate executives understand the importance of security. This can be seen from the satisfaction level of the questionnaire survey (see Fig. 5).
On the other hand, the number of participants did not reach the capacity of 200, which was less than last year.
The Kyushu University Cyber Security Center (CSC) has contributed to the security camp as one of the host organizations from this year, but it is thought that the invitation for participation was not sufficient because it has been less than a year since the center was established.
For next year, I think it is necessary to actively promote the activities of the security camp to meet the capacity.
Training camp course
The training camp course is also enriched as a content for security education and human resource development, and in particular, students not only interact with students of the same generation at other universities, but also with various security experts who are active in society. I felt that it was a place where I could study in a very meaningful environment because I could interact with them.
On the other hand, only one person participated in the training camp from Kyushu University. This is a disappointing result for the side that provided the venue.
In the future, I think it is necessary to appeal the existence of security camps to students in order to increase the number of students at Kyushu University.

